After too much time I have posted coWPAtty 4.5 with several fixes and a couple of new features:
- Fewer restrictions on collecting the data needed to mount an attack. The default behavior requires all 4 frames of the 4-way handshake to mount an attack. If you specify “-2” on the command-line, coWPAtty will only require frames 1 and 2 of the 4-way handshake to mount an attack. More on this below.
- Validate that the needed information is present to mount an attack, without launching the attack (the “-c” option). This was requested by Pure Hate for an awesome project he gave me a preview on. I’m hoping details of this project will be public soon.
The “-2” option also includes fewer restrictions for validating the content of the packet capture. This was implemented by a patch submitted by Nathan Grennan, accommodating some AP’s that do not strictly adhere to the IEEE 802.11i/IEEE 802.11-2007 specification.
Removing the restriction of needing all 4 frames of the 4-way handshake to mount an attack has some interesting implications. First, packet captures taken while channel hopping often miss parts of the 4-way handshake, since they can hop in the middle of the 4-way handshake exchange. Relying on only frames 1 and 2 gives you a better chance of catching the needed data even if you are channel hopping.
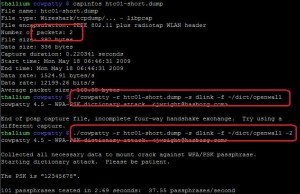
coWPAtty "-2" utilization example
Second, it provides the ability for an attacker to mount an attack against a client even if they aren’t within range of their target network (for example, a WPA2-PSK user is at the airport). Consider the following illustration:
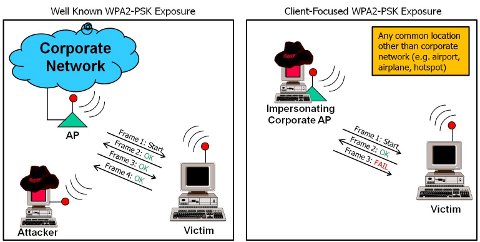
Cowpatty Attack Scenarios
On the left is an example of what I consider a traditional WPA2-PSK attack. The attacker gets within physical proximity of the target network and waits for (or coerces) the 4-way handshake between an AP and a valid client system.
On the right, however, is a less-understood attack scenario. In the 4-way handshake, the client system authenticates first, sending a HMAC-MIC of frame 2 to the AP. If an attacker impersonates the legitimate SSID of the network, they are able to send Frame 1 of the 4-way handshake (no authentication) and observe the HMAC-MIC of frame 2. At frame 2, the attacker has everything they need to recover the PSK (now with cowpatty’s “-2” option). Frame 3 fails validation by the client, but by that point, it’s too late.
In practice, I’m testing this using HostAP running on my attack workstation, but that’s not even necessary. Simply take any SOHO AP, configure the SSID to reflect that of your vistim with any pre-shared key and observe the exchange between the victim and the imposter AP, supplying the packet capture to coWPAtty with the “-2” option.
My transition to work for InGuardians has given me a chance to spend more time on penetration tests. As a result, I’ve started to change my mind about the value of “weaponized” attack tools. If the tool isn’t reliable, works under many circumstances and flexible enough to withstand an error or two, it takes much longer to be useful, and that costs your customer more. I’m using this as a motivator to make tools more effective, capable of demonstrating a point, and thereby allowing you to providing greater value to your customer.
I’d love to hear comments and questions. Please add a comment below, or send me a note.
-Josh