Microchip Zena Network Analyzer
A few days ago I bought a Microchip Zena ZigBee sniffer. This USB HID device comes with simple software for Windows that captures and decodes 2.4 GHz 802.15.4, ZigBee, MiWi (Microchip stack) and MiWi-P2P traffic. It’s $150, which is a little steep considering that it is a PIC18LF with USB and a MRF24J40 radio, but I’ve had fun playing with it all the same.
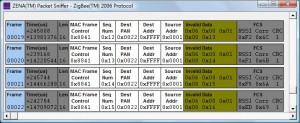
The Zena 3.0 sniffer software provides a basic per-packet view of frames. I guess we are all spoiled by Wireshark, but I was hoping for more detail and a better UI. The Zena sniffer can save a capture in a proprietary file format, and can export selected frames (to the clipboard) in space-delimited hex bytes.
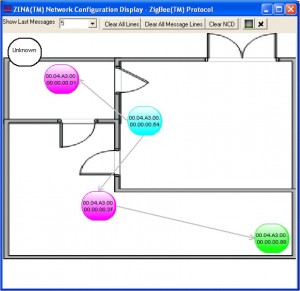
A cool accompanying feature is the network configuration display interface where Zena will identify all the parent/child relationships observed. You can specify a BMP background as a floorplan and move the nodes to their physical locations as well.
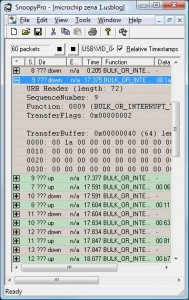
With no Linux support, I decided to write my own user space Linux driver to capture packets with the goal of integrating it into libpcap captures and other tools including Kismet Newcore. Plugging into a Linux box, it was clear that the device was using the USB HID, which was good news for me since it would be simpler to reverse the configuration details. Using the SnoopyPro USB sniffer, I was able to look at the USB packets, observing data from frames shown by the sniffer, as well as recording the configuration activity based on the channel I specified to capture on.
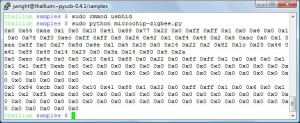
With this information, it was straightforward to identify the USB endpoint 0x01 as the control channel (for setting the channel) and USB endpoint 0x81 as the data endpoint (for delivering frames). Using PyUSB with the excellent Pymissle project by Scott Weston as an example, I quickly put together a tool that can set the channel number and capture frames from the Zena device, dumping the hex bytes to stdout.
The Python script is available here. It’s hack, but it was enough to get me started on what will be my next post: zbfind, a location tracking and identification tool for ZigBee and 802.15.4 networks.
-Josh