As a beat-my-tester for the RFIDler Kickstarter project, I got one of the first batch of these sweet LF RFID reader/writer/emulator units, straight from Zac Franken and Adam Laurie.
Although I have a Proxmark3 (actually, it’s not mine, it belongs to Larry Pesce, but he’s never getting it back), I am excited about the RFIDler as a low-cost alternative with active and exciting development.
When the RFIDler arrived it was running alpha3 firmware, which needed to be upgraded to the latest firmware in the RFIDler GitHub repository. Flashing requires the mphidflash utility, which is available in source or binary form on Google Code.
The mphidflash tool required libhid-dev on Ubuntu, but that package has been retired for a while as abandoned by the author. To get mphidflash working on Ubuntu, I grabbed the packages from Ubuntu 10.04 and installed them as shown:
$ wget http://mirrors.kernel.org/ubuntu/pool/universe/libh/libhid/libhid-dev_0.2.15+20060325-2.2ubuntu1_i386.deb $ wget http://mirrors.kernel.org/ubuntu/pool/universe/libh/libhid/libhid0_0.2.15+20060325-2.2ubuntu1_i386.deb $ sudo dpkg -i libhid0_0.2.15+20060325-2.2ubuntu1_i386.deb $ sudo dpkg -i libhid-dev_0.2.15+20060325-2.2ubuntu1_i386.deb $ wget http://mphidflash.googlecode.com/files/mphidflash-1.3-bin-linux.tar.gz $ tar xfz mphidflash-1.3-bin-linux.tar.gz $ sudo cp mphidflash /usr/sbin
After that, flashing the RFIDler becomes straightforward. First, download the GitHub repository files and change to the RFIDler/python directory, then run the setup.py script:
$ git clone https://github.com/ApertureLabsLtd/RFIDler.git Cloning into 'RFIDler'... WARNING: gnome-keyring:: couldn't connect to: /tmp/keyring-WsskxT/pkcs11: No such file or directory remote: Reusing existing pack: 518, done. remote: Counting objects: 16, done. remote: Compressing objects: 100% (13/13), done. remote: Total 534 (delta 1), reused 0 (delta 0) Receiving objects: 100% (534/534), 8.90 MiB | 1001 KiB/s, done. Resolving deltas: 100% (279/279), done. $ cd RFIDler/python $ sudo python setup.py install
Now you should be able to run the rfidler.py script to interact with the RFIDler hardware. Plug in the hardware and check the version on your hardware (you may need to run rfidler.py as root on your system):
$ rfidler.py /dev/ttyACM0 'VERSION' sending 'VERSION' 0003-alpha
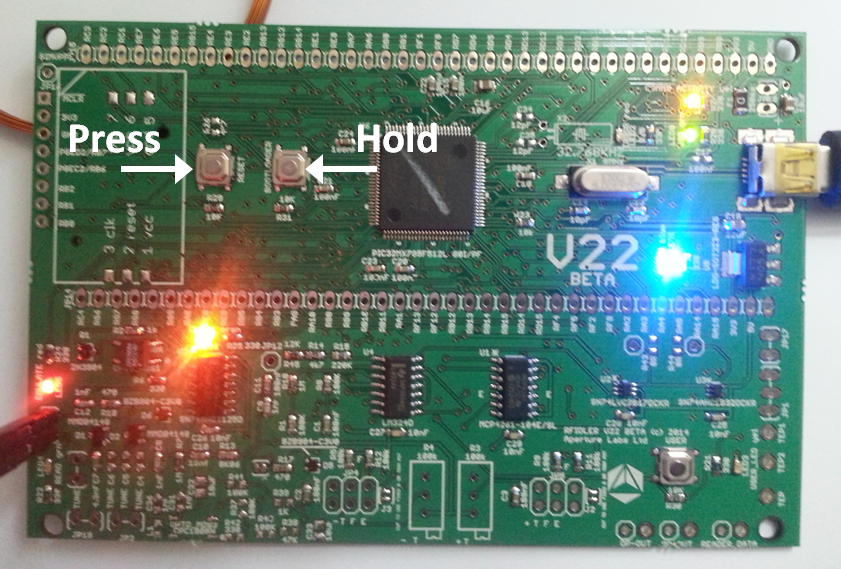
To update the firmware, hold the bootloader button and press “reset”. The LED07 and LED08 LED’s will start alternating amber and green.
You will also see a kernel message indicating that the device has entered into bootloader mode.
$ dmesg | grep Bootloader [783265.119771] generic-usb 0003:04D8:003C.0006: hiddev0,hidraw2: USB HID v1.11 Device [Microchip Technology Inc. USB HID Bootloader] on usb-0000:02:00.0-2.1/input0
Now, change to the head of the RFIDler directory and flash the device (lots of the status dots have been removed below):
$ sudo mphidflash -r -w firmware/Pic32/RFIDler.X/dist/debug/production/RFIDler.X.production.hex [sudo] password for jwright: USB HID device found: 503808 bytes free Erasing... Writing hex file 'firmware/Pic32/RFIDler.X/dist/debug/production/RFIDler.X.production.hex':.................................................................................................................................. Verifying:.................................................................................................................................. Resetting device... $ rfidler.py /dev/ttyACM0 version sending 'VERSION' 0019-beta
Voila!
-Josh
 A special thanks to Horst Karin for posting a great review of my new book,
A special thanks to Horst Karin for posting a great review of my new book,