On Thursday night at 7pm EDT (4pm PDT) I’ll be giving a special evening webcast called “Budget Wireless Assessment using Kismet-Newcore“. I delivered this content at the SANS Denver conference a few weeks ago, but several people have contacted me complaining that they wanted to get in on the new features Kismet has to offer including plugins, new security framework, the new user interface, integrated graph views and more.
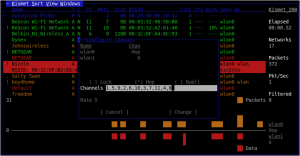
For example, did you know that Kismet Newcore has the ability to apply fine-grained channel hopping controls, allowing you to easily configure Kismet to spend more time on commonly used channels (such as channels 1, 6 and 11)? This allows you to focus the data collection process while not missing any AP’s that might on uncommon channels.
The webcast will use the SANS vLive! (formerly @Home) setup based on Elluminate. This software gives me the ability to do live demonstrations during the webcast with a Q+A interface and the ability for viewers to ask questions during the session.
What’s more, attendees will get a 10% discount code off my upcoming Ethical Hacking Wireless course, delivered in manageable 3-hour chunks once a week for 12 weeks, starting September 7th. More information on the Ethical Hacking Wireless vLive! course is available at http://www.sans.org/athome/details.php?nid=19608.
Sign up for the webcast today! https://www.sans.org/webcasts/show.php?webcastid=92713
-Josh