A patch for the popular open-source FreeRADIUS implementation to demonstrate RADIUS impersonation vulnerabilities by Joshua Wright and Brad Antoniewicz. This patch adds the following functionality:
- Simplifies the setup of FreeRADIUS by adding all RFC1918 addresses as acceptable NAS devices;
- Simplifies the setup of EAP authentication by including support for all FreeRADIUS supported EAP types;
- Adds WPE logging in $prefix/var/log/radius/freeradius-server-wpe.log, can be controlled in radius.conf by changing the “wpelogfile” directive;
- Simplified the setup of user authentication with a default “users” file that accepts authentication for any username;
- Adds credential logging for multiple EAP types including PEAP, TTLS, LEAP, EAP-MD5, EAP-MSCHAPv2, PAP, CHAP and others
For setup information, see the SETUP section below, or our slides from Shmoocon 4.
News
May 18 2010
Brad brought the FreeRADIUS-WPE patch up to date for FreeRADIUS 2.1.7. It’s amazing to me that lots of people seemed to have missed this issue in PEAP and other EAP methods, as it’s still extremely useful in most of the pen-tests I engage in.
July 18 2008
I’ve been working on extending the FreeRADIUS-WPE attack to also compromise EAP/TLS networks as well. It’s still a work-in-progress, but I think it will be cool when it’s finished. Stay tuned.
February 18 2008
Thanks to everyone who made it out to our presentation at Shmoocon 2008 where we debuted FreeRADIUS Wireless Pwnage Edition. Check out our slides, and you can get the patch for freeradius-wpe below. Drop me a note with any questions. -Josh
Screenshots
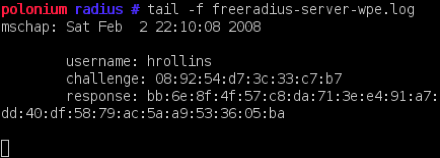
Download
- FreeRADIUS 2.1.7 patch (MD5: 20f48de7689bbff00acb5c8b46c71c20)
- FreeRADIUS 2.0.2 patch (MD5: 6671917d602373d8010fe38de66377e4)